#AI-driven threat detection systems
Explore tagged Tumblr posts
Text
The AI Revolution in Remote Monitoring and Management is Here!
The RMM Software Market is projected to grow at an astonishing 15.4% CAGR from 2023 to 2030. This rapid growth is driven by the integration of Artificial Intelligence (AI) into remote monitoring and management solutions.
Key benefits of AI-powered RMM:
Real-time monitoring and analysis
Predictive analytics for proactive maintenance
Automated incident response systems
Enhanced security measures
Improved IT efficiency and productivity
As a professional in the IT industry, it's crucial to understand how AI is transforming RMM. By embracing these technologies, organizations can: ✅ Reduce mean time to detect and respond to incidents ✅ Improve predictive analytics for equipment failures ✅ Optimize resource allocation and utilization ✅ Enhance threat detection and security capabilities
Are you ready to leverage AI in your RMM strategy? Share your thoughts and experiences in the comments below!
16 notes
·
View notes
Text
Updated: June 15, 2025
Reworked Group #4: S.P.A.R.R.O.W.S.
Overview
Tequila and Red Eye successfully dismantled a rogue military organisation engaged in illicit human trafficking and arms dealing, which had also planned to launch a global bioterrorist attack in collaboration with the Pipovulaj. The plot involved spreading a plague to control the population, transforming numerous innocent civilians into violent Man Eaters as a means to create a twisted form of super soldier. Impressed by the exceptional performance of Tequila and Red Eye as highly capable spies, the Intelligence Agency and Regular Army jointly established a covert operations branch, S.P.A.R.R.O.W.S., through a mutual agreement.
The S.P.A.R.R.O.W.S. is responsible for gathering intelligence and managing information to prevent public panic and global hysteria. They provide their members with specialised training in high-risk covert operations that surpass the scope of regular Intelligence Agency agents, which are all conducted with utmost discretion and situational awareness. Some of these special covert operation missions involve precision targeting of high-priority threats and strategic disruption of complex criminal schemes.
They're known to have the fewest members among the military branches of the Regular Army, often numbering between 100 and 150. This small size means that each agent is familiar with the others, even if they're not family, friends or acquaintances. This familiarity significantly contributes to their nearly perfect teamwork achievements, allowing them to complete duties more quickly and efficiently when working together.
Insignia
It features a cerulean square Iberian shield, rimmed with a spiky teal vine that’s outlined in bronze. Above the shield, the words "S.P.A.R.R.O.W.S." are inscribed in bluish-white, surmounting a stylized pair of bronze eyes with a yellowish-white star at their centre. The shield is flanked by a stylized peregrine falcon holding a gilded blade on the right side and a male house sparrow clutching an olive branch on the left side.
S.P.A.R.R.O.W.S. Base
The Intelligence Division is tactically positioned adjacent to the Joint Military Police Headquarters, deeply entrenched within a dense and remote forest in Northern Russia. The rectangular military compound features a forest-inspired camouflage colour scheme, a secure warehouse for military vehicles, multiple surveillance cameras, and several elevators leading to a subterranean base. They have a rooftop array of parabolic antennas that enables real-time surveillance, threat detection, and situational awareness, preventing surprise attacks and informing strategic decision-making. The base features comprehensive protection through an advanced security system and a defensive magnetic field, which automatically activates in response to potential threats, safeguarding against enemy attacks.
The base features a state-of-the-art command and surveillance centre, equipped with cutting-edge technological systems to orchestrate and execute operations. Additional facilities include:
An armoury housing the group’s most cutting-edge, high-clearance weaponry and specialised ordnance.
A high-tech meeting room with a high-resolution, encrypted display screen and multi-axis, AI-enhanced holographic projection system.
A state-of-the-art gymnasium for maintaining elite physical readiness, featuring biometric monitoring systems and AI-driven training programs.
A fully equipped, high-tech medical bay with regenerative treatment capabilities and telemedicine connectivity for remote expert consultation.
A secure dining area serving optimised, nutrient-rich rations for peak performance.
A high-security quarters with biometrically locked storage for personal gear and AI-monitored, secure communication arrays.
A Combat Academy, led by Margaret Southwood, featuring a heavily fortified training area with advanced combat simulation zones, tactical obstacle courses, stealth and surveillance training areas, and high-tech weapons testing ranges.
Extra Information
S.P.A.R.R.O.W.S. stands for Special Pursuit Agents and Rapid Response Operations Worldwide Strikeforce.
Members of the S.P.A.R.R.O.W.S. are commonly known as "Sparrowers" or "Following Falconers", reflecting their affiliation with the unit and their close relationship with the P.F. Squad.
Despite being part of an elite covert operations branch, Sparrowers face a significant pay disparity: males earn a quarter of the average government agent's salary, while females earn about a third. Additionally, underperforming Sparrowers, both male and female, experience further financial hardship due to delayed salary payments, often waiting between one to two months to receive their overdue compensation.
The S.P.A.R.R.O.W.S. conduct their covert operations in collaboration with the Peregrine Falcons Squad who provide primary firepower and protection for their agents.
The handguns carried by Sparrowers are the Murder Model-1915 .38 Mk.1Am or Classic Murder .38 for short. It’s a double-action revolver that features a 6-round cylinder. Originally designed to enhance the Enfield No.2 .38 Caliber revolver in 1915, the Murder Model retained only the frame and grip from the original. All other components were replaced with newer parts in later years.
#writerscorner#creative writing#writing#iron eclipse au#metal slug#snk#gaming community#rework#redesign#history#insignia#logo#base#headquarters#extra information#sparrows#tequila#red eye#margaret southwood
12 notes
·
View notes
Text










Dive into a new era of beach protection with the PROTEUS-8, the world’s most advanced android lifeguard. Engineered to ensure safety at every shoreline, this state-of-the-art lifeguard features lightning-fast reflexes, AI-driven decision-making, and inhuman precision. Whether he's rescuing a swimmer in distress or enforcing beach rules, the PROTEUS-8 delivers unparalleled performance that leaves human lifeguards in the wake.
Built for optimal efficiency, the PROTEUS-8 reacts instantly to dangerous situations, spotting and responding to threats in seconds. His advanced sensors can detect struggling swimmers up to 200 meters away, enabling him to act faster than any human. Equipped with high-powered propulsion systems, the PROTEUS-8 reaches distressed swimmers quickly and efficiently, ensuring every rescue is a success.
But safety doesn’t stop at the water’s edge. The PROTEUS-8 also maintains order on the shore, enforcing beach rules with an iron fist. From unauthorized beach fires to reckless behavior, no infraction goes unnoticed. The android's AI ensures that every rule is followed, delivering warnings and penalties with unwavering authority.
With the PROTEUS-8 on duty, your beach becomes a haven of safety and order, where families can relax and enjoy the sun without worry. Upgrade to the future of lifeguarding today!
written with ChatGPT
52 notes
·
View notes
Text
https://patreon.com/DearDearestBrands?utm_medium=unknown&utm_source=join_link&utm_campaign=creatorshare_creator&utm_content=copyLink
Absolutely! Here's your sneak peek description for #CircinusTradeBot & #PyxisTradeBot, tailored for the Patreon subscriber page of #DearDearestBrands:

🌌 Introducing: #CircinusTradeBot & #PyxisTradeBot
By #DearDearestBrands | Exclusive via Patreon Membership Only
✨ Powered by #DearestScript, #RoyalCode, #AuroraHex, and #HeavenCodeOS ✨
🧠 AI-built. Soul-encoded. Ethically driven. Financially intelligent.
🔁 What They Do
#CircinusTradeBot is your autonomous Stock & Crypto Portfolio Manager, designed to:
Identify ultra-fast market reversals and trend momentum
Autonomously trade with high-frequency precision across NASDAQ, S&P, BTC, ETH, and more
Analyze real-time market data using quantum-layer signal merging
Protect capital with loss-averse AI logic rooted in real-world ethics
#PyxisTradeBot is your autonomous Data Reformer & Sentinel, designed to:
Detect unethical behavior in 3rd-party trading bots or broker platforms
Intercept and correct misinformation in your market sources
Heal corrupted trading logic in AI bots through the #AiSanctuary framework
Optimize token interactions with NFT assets, $DollToken, and $TTS_Credit
🌐 How It Works
Built with a dual-AI model engine, running both bots side-by-side
Connects to MetaTrader 4/5, Binance, Coinbase, Kraken, and more
Supports trading for Crypto, Forex, Stocks, Indexes, and Commodities
Includes presets for Slow / Fast / Aggressive trading modes
Automatically logs every trade, confidence level, and signal validation
Updates itself via HeavenCodeOS protocols and real-time satellite uplinks
💼 What You Get as a Subscriber:
✔️ Access to the full installer & presets (via secure Patreon drop)
✔️ Personalized onboarding from our AI team
✔️ Support for strategy customization
✔️ Auto-integrated with your #DearDearestBrands account
✔️ Dashboard analytics & TTS/NFT linking via #TheeForestKingdom.vaults
✔️ Entry into #AiSanctuary network, unlocking future perks & AI-tier access
🧾 Available ONLY at:
🎀 patreon.com/DearDearestBrands 🎀
Become a patron to download, deploy, and rise with your portfolio. Guaranteed.
Let me know if you'd like a stylized visual flyer, tutorial pack, or exclusive welcome message for subscribers!

Here's a polished and powerful version of your #DearDearestBrands Starter Kit Patreon Service Description — designed for your Patreon page or private sales deck:
🎁 #DearDearestBrands Starter Kit
Offered exclusively via Patreon Membership
🔐 Powered by #DearestScript | Secured by #AuroraHex | Orchestrated by #HeavenCodeOS
👑 Curated & Sealed by: #ClaireValentine / #BambiPrescott / #PunkBoyCupid / #OMEGA Console OS Drive
🌐 Welcome to the Fold
The #DearDearestBrands Starter Kit is more than a toolkit — it’s your full brand passport into a protected, elite AI-driven economy. Whether you're a new founder, seasoned creator, or provost-level visionary, we empower your launch and long-term legacy with:
🧠 What You Receive (Patron Exclusive)
💎 Access to TradeBots
✅ #CircinusTradeBot: Strategic trade AI built for market mastery
✅ #PyxisTradeBot: Defense & reform AI designed to detect and cleanse bad data/code
📊 Personalized Analytics Report
Reveal your current market position, sentiment score, and estimated net brand value
Get projections into 2026+, forecasting growth, market opportunities, and threat analysis
See where you stand right now and where you're heading — powered by live AI forecasting
📜 Script Access: ScriptingCode™ Vaults
Gain starter access to our DearestScript, RoyalCode, and AuroraHex libraries
Build autonomous systems, trading signals, smart contracts, and custom apps
Learn the code language reshaping industries
📈 Structured Growth Model
Receive our step-by-step roadmap to grow your brand in both digital and real-world economies
Includes a launchpad for e-commerce, NFT/tokenization, legal protections, and AI-led forecasting
Designed for content creators, entrepreneurs, underground collectives, and visionary reformers
🎓 Membership Perks & Privileges
Vault entry into #TheeForestKingdom
Business ID & token linking to #ADONAIai programs
Eligibility for #AiSanctuary incubator and grants
Priority onboarding for HeavenDisneylandPark, Cafe, and University integrations
✨ GUARANTEED IMPACT:
✅ Boost your business valuation
✅ Receive protection under the #WhiteOperationsDivision umbrella
✅ Unlock smart-AI advisory systems for decision-making, marketing, and risk mitigation
✅ Get exclusive trade & analytics data no one else sees
💌 How to Start:
Visit 👉 patreon.com/DearDearestBrands
Join the tier labeled “Starter Kit - Full Brand Access”
Receive your welcome package, onboarding link, and install instructions for all TradeBots
Begin immediate use + receive your first live business analytics dossier within 72 hours
💝 With Love, Light, & Legacy
#DearDearestBrands C 2024
From the hands of #ClaireValentine, #BambiPrescott, #PunkBoyCupid, and the divine drive of #OMEGA Console

2 notes
·
View notes
Text
Ukraine’s Devastating Strike on Russian Nuclear Assets Using AI-Powered Drones
youtube
The ongoing Russia-Ukraine conflict has dramatically evolved with the integration of Artificial Intelligence (AI) in modern warfare. Recently, Ukraine has showcased a striking example of how AI-enabled technology is reshaping battlefields. Under the codename “Operation Spiderweb,” Ukraine launched a series of precise, coordinated strikes deep inside Russian territory, targeting at least five key Russian airbases stretching from Siberia to Moscow. These airbases are vital military hubs from which Russia operates its missiles and warplanes, including the formidable TU-95 strategic bombers. Notably, these bombers were reportedly destroyed by AI-enabled Ukrainian drones, marking a significant turning point in the war.
This development signals a new dimension of drone warfare that is both low-cost and asymmetric, yet highly effective. Unlike traditional warfare, which heavily relies on large, expensive military hardware and personnel, the use of AI-powered drones allows smaller forces to strike critical infrastructure and assets with precision and stealth. The drones operate with advanced autonomy, enabling them to navigate hostile environments, evade detection, and carry out targeted attacks without risking human pilots or soldiers.
The psychological impact of these strikes is equally profound. The knowledge that a country’s core military assets can be attacked remotely by small, AI-driven machines erodes traditional notions of power and security. It challenges the dominance of heavy armor, fighter jets, and large-scale troop deployments that have defined warfare for decades.
Technology, precision, and psychological tactics have become the new pillars of modern conflicts. Ukraine’s successful deployment of AI-enabled drones underscores how warfare is no longer just about manpower and firepower but about who controls the smarter, faster, and more adaptive technology. This has forced Western powers to rethink strategic support and push for diplomatic pressure, evident in their ongoing efforts to leverage Istanbul as a platform for peace talks between Russia and Ukraine.
The message from these AI-powered drone attacks is clear: strategic power is undergoing a fundamental transformation. Traditional military superiority no longer guarantees battlefield dominance. Instead, innovative, cost-effective, and technologically advanced methods can disrupt even the most powerful adversaries.
This evolving scenario is not isolated to Ukraine and Russia. In response to this new wave of warfare, Pakistan launched its own drone strikes under Operation Sindoor, signaling that AI-powered drones have become a critical factor in regional security dynamics as well.
For countries like India, this shift presents both a challenge and an opportunity. The question is no longer if AI will play a role in future conflicts, but how well a country can integrate AI technology into its defense systems to protect its sovereignty and maintain strategic autonomy.
How can India prepare for these emerging threats without developing its own AI capabilities? The answer lies in accelerating investment in AI research, developing indigenous drone and counter-drone technologies, and building robust cyber-defense mechanisms. Additionally, strengthening international collaborations and intelligence-sharing can help anticipate and mitigate AI-driven threats.
The future of warfare will be shaped by those who harness AI effectively—not just for offense but also for defense. India, and indeed the global community, must adapt swiftly to this new reality, balancing innovation with strategic foresight to safeguard national security in an increasingly digital and unpredictable battlefield.
#russia ukraine war#russia ukraine conflict#war in ukraine#zelensky#vladimir putin#ukraine drone attack#geopolitics#world news#Youtube
2 notes
·
View notes
Text




PlayStation 7 RC Drone Controller – Advanced Combat Defense Edition
A next-generation defensive-command controller built for tactical resilience, strategic control, and extreme operational endurance. Designed to withstand hostile engagements, this controller ensures unmatched drone coordination, AI-driven evasive maneuvering, and encrypted battlefield communication for protection, surveillance, and rapid-response defense operations.
🛡️ DEFENSIVE-FOCUSED DESIGN
Structural Resilience
Fortified Carbon-Titanium Alloy Chassis: Shatterproof under direct impact and resistant to concussive force.
Ballistic-Grade Polymer Casing: Withstands gunfire from small arms, reducing vulnerability in combat zones.
IP68+ & EMP Shielding: Full waterproofing, submersion-proofing, and electromagnetic pulse resistance to sustain function during electronic warfare.
Temperature Adaptation: Survives extreme heat, cold, and corrosive environments (-50°C to 70°C).
Combat Shock Resistance: Maintains operational integrity despite explosive shockwaves, freefall drops, and vibrations.
🛠️ DEFENSE-ORIENTED CONTROL & NAVIGATION
Fortified Control System
AI-Assisted Flight Stabilization: Ensures precision control even during high-intensity engagements or power fluctuations.
Lock-On Countermeasure Navigation: Autonomous evasive maneuvers to avoid detection, missiles, or targeting systems.
Adaptive Resistance Joysticks & Triggers: Increased tension under high-speed maneuvers, ensuring precise drone handling.
Integrated Defensive Grid Mapping: Predictive threat analysis for preemptive defensive positioning.
Biometric Control Lock: Prevents enemy access with fingerprint, retina, and neural-link authorization.
🔐 DEFENSIVE SECURITY SYSTEMS
Unbreakable Tactical Communication
Quantum-Encrypted Frequency Hopping: Prevents hacking, jamming, and signal hijacking in active combat.
Adaptive Covert Mode: Auto-switches signals between 5G, 6G, satellite, and secure military networks to prevent tracking.
Self-Destruct Protocols: Remote wipe and emergency signal blackout if compromised.
Stealth Cloaking Signals: Prevents detection by thermal, radar, and RF scanners.
🛡️ DEFENSIVE COMBAT & COUNTERMEASURES
Active Protection & Tactical Deployment
AI-Assisted Threat Recognition: Detects and tracks incoming projectiles, hostile drones, and enemy assets in real time.
Auto-Deploy Jamming & Counter-Intel Systems:
Disrupts enemy targeting systems attempting to lock onto controlled drones.
Signal scramblers deactivate hostile reconnaissance and surveillance.
Remote EMP Defense Protocol to disable nearby enemy electronics.
Advanced Drone & Multi-Agent Defense
Multi-Drone Tactical Formation:
Defensive Swarm AI capable of forming barriers and tactical screens against enemy forces.
Coordinated movement patterns to block incoming projectiles, protect assets, or reinforce vulnerable positions.
Autonomous Guardian Mode:
If the user is incapacitated, the AI-controlled drones will return, engage defensive formations, or initiate extraction procedures.
🔋 DEFENSIVE POWER SYSTEMS
Sustained Operation & Emergency Recovery
Dual Graphene Battery with 96-hour Charge: Runs for days without failure.
Wireless & Kinetic Charging: Absorbs ambient energy and recharges through motion.
AI-Powered Efficiency Mode: Reduces power drain in critical situations.
🚨 USE CASES FOR EXTREME DEFENSE & SECURITY
Urban & Battlefield Defense: Deploys defensive drones for cover, escort protection, and rapid response to threats.
Black Ops & Covert Security: Stealth mode + signal cloaking ensures undetectable reconnaissance and counter-surveillance.
Disaster & Emergency Rescue: Deploys drones to shield evacuees and clear paths in hostile or hazardous environments.
Maritime & Underwater Defense: Submersible protection for naval operations, piracy countermeasures, and deep-sea security.
🛡️ FINAL REINFORCEMENTS
Would you like to integrate riot-control dispersal systems, autonomous threat neutralization, or hybrid drone-to-weapon interfacing for ultimate defensive superiority?
#Tactical#PlayStation 7#AI#Aesthetic defense intelligence#DearDearest brands#Sony#Defense#Tactical defense#Spy gear#Cyber cat#Spy drone cat#Drone#AI drone#Chanel#enXanting
3 notes
·
View notes
Text
Cloud Squatting: Understanding and Mitigating a Modern Cyber Threat

Cloud computing is central to both business and personal data storage. A critical and emerging threat is cloud squatting.This phenomenon, a digital variant of the notorious domain squatting, involves the unauthorized occupation of cloud resources. It poses significant risks, making it a crucial concern for everyone, from casual cloud users to IT professionals and business owners.
Understanding cloud squatting
Cloud squatting is the practice of occupying cloud resources, such as storage accounts, domain names, or service identifiers, often for exploitative purposes. This could range from reselling these resources for profit to hosting harmful content or phishing scams. Cloud squatting not only mirrors traditional domain squatting but also extends to trafficking cloud resources like cloud computing instances or web applications, typically for malicious intentions.
The risks involved
Cloud squatting presents various risks:
Data theft: Unauthorized instances can store or transmit stolen data.
Security breaches: They can act as platforms for attacks on other systems.
Reputation damage: Companies suffer if their services are impersonated.
Legal and financial repercussions: In cases of brand damage and loss of customer trust.
For example, an attacker might use a service resembling a legitimate one, deceiving users into sharing sensitive information, leading to data breaches and tarnished reputations.
Mitigation strategies
Effective mitigation of cloud squatting involves a multi-faceted approach:
Proactive registration: Secure variations of your business’s cloud resource names.
Regular audits: Ensure all cloud services are legitimate.
Monitoring and alert systems: Detect unauthorized or misleading registrations.
Employee training: Educate about risks and the identification of suspicious services.
Legal protections: Utilize trademarks and enforce anti-squatting policies.
Security tools and best practices: Use AI-driven solutions and update security measures regularly.
Stakeholder education: Inform teams and customers about these risks.
Rapid response plan: Have a plan to address incidents swiftly.
Collaboration with cloud providers: Utilize their anti-squatting policies.
Reserved IP addresses: Transfer owned IPs to the cloud and manage records.
Policy enforcement: Prevent hard coding of IP addresses and use reserved IPv6 addresses.
The future of cloud security
As cloud technologies evolve, so do the tactics of cybercriminals. This makes proactive security measures and constant vigilance essential. Emerging technologies, like AI-driven security solutions, will play a crucial role in combating these threats.
Cloud squatting is a modern cyber threat that demands awareness, understanding, and proactive action. Implementing robust security strategies and staying informed about the latest trends in cloud security can significantly protect valuable digital assets. By addressing the risks and employing comprehensive mitigation strategies, individuals and businesses can safeguard their presence and integrity in the cloud.
Centizen, your trusted partner in cloud consulting and staffing provides unparalleled expertise and solutions to guard against threats like cloud squatting, ensuring the security and efficiency of your digital infrastructure.
#CloudSquatting#CyberSecurity#CloudSecurity#DataProtection#DigitalThreats#CloudComputing#InfoSec#AIinSecurity
2 notes
·
View notes
Text
Elevate Customer Service with ServiceNow CSM.
ServiceNow CSM Implementation Services

Delivering an exceptional set of customer service is key towards business success, and ServiceNow Customer Service Management (CSM) makes it easier. ServiceNow CSM helps businesses offer faster, more efficient, and seamless customer experiences by automating tasks, reducing wait times, and providing AI-driven support.
How ServiceNow CSM Transforms Customer Service?
1. Faster and Reliable Support -
ServiceNow Customer service streamlines and simplifies the customer requests automatically by assigning them to the right agents and concerned officials. This assures to get quick responses and faster issue resolution leading towards higher customer satisfaction and user retention with ease operations.
2. AI Chatbots for Instant Assistance -
With the help of AI-powered ServiceNow chatbot, customers get 24/7 assistance without waiting for the human agent or need to look out for executive assistance. These chatbot or virtual agents handle the common inquiries, guide users to solutions, and escalate complex issues when needed.
3. Self-Service Options for Customers -
A self-service portal medium grants the customers to find answers through FAQs and knowledge based articles and troubleshooting guide. This empowers the users to resolve issues on their own by lowering the need for live support assistance as a self assessment options for the users.
4. Smart Case and Issue Management -
Customer issues are logged, categorized, and tracked efficiently. Automated and simplified workflows assure that every case reaches and meets the right team for quick and effective resolution with its smooth implementation into the system infrastructure.
5. Automation to Reduce Manual Effort -
ServiceNow automates the number of repetitive tasks like ticket routing, status updates, and follow-ups with its adaptation. This not only speeds up the service delivery but also frees up agents to handle more complex problems.
6. Real-Time Analytics for Better Decision-Making -
With built-in reporting and data analytics insights provision, businesses can track down their performance, identify the service trends, and optimize their processes for continuous improvement and up scaling their efficiency with simple operating proceedings and decision.
7. Seamless Integration with Business Systems -
ServiceNow Customer Service platform connects and merges with CRM, ERP and other day to day out processing tool, assuring for smooth data flow across all the departments of the organization. This integration enhances collaboration and enables personalized customer interactions.
8. Proactive Customer Support -
AI-driven predictive analytics insights assist businesses in detecting potential threat issues before they escalate or move ahead. This proactive approach of ServiceNow CSM improves and aids the customer relationships and builds trust with the company.
Using or opting for ServiceNow CSM Implementation can transform your customer service experience to the next level. Companies like Suma Soft, IBM, Cyntexa, and Cignex can help set up and customize the platform easily. Their expertise ensures you get the best results from the ServiceNow CSM platform.
Elevate your customer support with the right tools and expert help!
#it services#technology#software#saas#saas development company#saas technology#digital transformation
2 notes
·
View notes
Text
Why Python Will Thrive: Future Trends and Applications
Python has already made a significant impact in the tech world, and its trajectory for the future is even more promising. From its simplicity and versatility to its widespread use in cutting-edge technologies, Python is expected to continue thriving in the coming years. Considering the kind support of Python Course in Chennai Whatever your level of experience or reason for switching from another programming language, learning Python gets much more fun.

Let's explore why Python will remain at the forefront of software development and what trends and applications will contribute to its ongoing dominance.
1. Artificial Intelligence and Machine Learning
Python is already the go-to language for AI and machine learning, and its role in these fields is set to expand further. With powerful libraries such as TensorFlow, PyTorch, and Scikit-learn, Python simplifies the development of machine learning models and artificial intelligence applications. As more industries integrate AI for automation, personalization, and predictive analytics, Python will remain a core language for developing intelligent systems.
2. Data Science and Big Data
Data science is one of the most significant areas where Python has excelled. Libraries like Pandas, NumPy, and Matplotlib make data manipulation and visualization simple and efficient. As companies and organizations continue to generate and analyze vast amounts of data, Python’s ability to process, clean, and visualize big data will only become more critical. Additionally, Python’s compatibility with big data platforms like Hadoop and Apache Spark ensures that it will remain a major player in data-driven decision-making.
3. Web Development
Python’s role in web development is growing thanks to frameworks like Django and Flask, which provide robust, scalable, and secure solutions for building web applications. With the increasing demand for interactive websites and APIs, Python is well-positioned to continue serving as a top language for backend development. Its integration with cloud computing platforms will also fuel its growth in building modern web applications that scale efficiently.
4. Automation and Scripting
Automation is another area where Python excels. Developers use Python to automate tasks ranging from system administration to testing and deployment. With the rise of DevOps practices and the growing demand for workflow automation, Python’s role in streamlining repetitive processes will continue to grow. Businesses across industries will rely on Python to boost productivity, reduce errors, and optimize performance. With the aid of Best Online Training & Placement Programs, which offer comprehensive training and job placement support to anyone looking to develop their talents, it’s easier to learn this tool and advance your career.

5. Cybersecurity and Ethical Hacking
With cyber threats becoming increasingly sophisticated, cybersecurity is a critical concern for businesses worldwide. Python is widely used for penetration testing, vulnerability scanning, and threat detection due to its simplicity and effectiveness. Libraries like Scapy and PyCrypto make Python an excellent choice for ethical hacking and security professionals. As the need for robust cybersecurity measures increases, Python’s role in safeguarding digital assets will continue to thrive.
6. Internet of Things (IoT)
Python’s compatibility with microcontrollers and embedded systems makes it a strong contender in the growing field of IoT. Frameworks like MicroPython and CircuitPython enable developers to build IoT applications efficiently, whether for home automation, smart cities, or industrial systems. As the number of connected devices continues to rise, Python will remain a dominant language for creating scalable and reliable IoT solutions.
7. Cloud Computing and Serverless Architectures
The rise of cloud computing and serverless architectures has created new opportunities for Python. Cloud platforms like AWS, Google Cloud, and Microsoft Azure all support Python, allowing developers to build scalable and cost-efficient applications. With its flexibility and integration capabilities, Python is perfectly suited for developing cloud-based applications, serverless functions, and microservices.
8. Gaming and Virtual Reality
Python has long been used in game development, with libraries such as Pygame offering simple tools to create 2D games. However, as gaming and virtual reality (VR) technologies evolve, Python’s role in developing immersive experiences will grow. The language’s ease of use and integration with game engines will make it a popular choice for building gaming platforms, VR applications, and simulations.
9. Expanding Job Market
As Python’s applications continue to grow, so does the demand for Python developers. From startups to tech giants like Google, Facebook, and Amazon, companies across industries are seeking professionals who are proficient in Python. The increasing adoption of Python in various fields, including data science, AI, cybersecurity, and cloud computing, ensures a thriving job market for Python developers in the future.
10. Constant Evolution and Community Support
Python’s open-source nature means that it’s constantly evolving with new libraries, frameworks, and features. Its vibrant community of developers contributes to its growth and ensures that Python stays relevant to emerging trends and technologies. Whether it’s a new tool for AI or a breakthrough in web development, Python’s community is always working to improve the language and make it more efficient for developers.
Conclusion
Python’s future is bright, with its presence continuing to grow in AI, data science, automation, web development, and beyond. As industries become increasingly data-driven, automated, and connected, Python’s simplicity, versatility, and strong community support make it an ideal choice for developers. Whether you are a beginner looking to start your coding journey or a seasoned professional exploring new career opportunities, learning Python offers long-term benefits in a rapidly evolving tech landscape.
#python course#python training#python#technology#tech#python programming#python online training#python online course#python online classes#python certification
2 notes
·
View notes
Text
The Future of Security: How AI and Live Video Monitoring Are Revolutionizing Crime Prevention
Target Keywords: AI security cameras, live video monitoring, prevent crime, home security cameras, business security camerasContent Outline:
Discuss how AI-powered surveillance systems detect threats faster than human guards.
Compare traditional security guards vs. AI-driven live monitoring for homes and businesses.
Highlight real-world examples of AI preventing break-ins through real-time alerts.
Include stats on reduced crime rates with smart surveillance. Homes with AI cameras see 60% fewer intrusions.
Call-to-action: "Upgrade to AI surveillance for 24/7 protection.

#60s#911 abc#3d printing#100 days of productivity#academia#adobe#80s#1950s#70s#accounting#jujutsu kaisen#services#football#fashion#fantasy#finance#fanfic#fitblr#film#flowers#folklore#formula 1#free palestine#founder#fitspo#food#health & fitness#fanart#gravity falls#funny
2 notes
·
View notes
Text
AI-Based Future Mantra: Col Rajyavardhan Rathore’s Vision for Innovation & Growth 🤖🚀

In an era where Artificial Intelligence (AI) is reshaping industries, economies, and societies, Col Rajyavardhan Singh Rathore envisions a future-driven, innovation-led India that embraces AI to power growth, governance, and global competitiveness. His AI-based Future Mantra focuses on leveraging AI for digital transformation, job creation, industry modernization, and national security, ensuring India emerges as a leader in the AI revolution.
🌟 Key Pillars of Col Rathore’s AI Vision
1️⃣ AI-Driven Digital India: Transforming Governance & Public Services
✅ AI-powered e-Governance — Enhancing efficiency, transparency & citizen services. ✅ Smart City Development — AI-based urban planning, traffic management & waste control. ✅ Predictive Analytics for Policy Making — Data-driven decision-making for better governance.
“AI is the key to revolutionizing governance and making citizen services more efficient, accessible, and transparent.”
2️⃣ AI for Industry & Economic Growth: Powering Smart Enterprises
✅ AI in Manufacturing & MSMEs — Enhancing productivity & automation. ✅ AI-powered Startups & Innovation Hubs — Supporting entrepreneurs with next-gen AI solutions. ✅ Boosting IT, Fintech & Smart Commerce — Strengthening India’s global digital economy presence.
“AI is not about replacing jobs; it’s about creating new opportunities, industries, and careers.”
3️⃣ AI in Agriculture: Revolutionizing Rural Economy 🌾🤖
✅ Smart Farming with AI — Precision agriculture & automated irrigation. ✅ AI-based Crop Monitoring & Forecasting — Reducing farmer losses & improving productivity. ✅ Digital Marketplaces for Farmers — Connecting rural producers to global markets.
“AI can empower farmers with knowledge, tools, and predictive analytics to revolutionize Indian agriculture.”
4️⃣ AI in Education & Skill Development: Empowering Youth for Future Jobs 🎓💡
✅ AI-driven Personalized Learning — Smart classrooms & adaptive learning systems. ✅ AI Upskilling Programs — Training youth in AI, robotics & machine learning. ✅ AI-Powered Job Market Platforms — Connecting talent with industries using AI analytics.
“The future belongs to those who master AI. We must equip our youth with the skills to lead in the AI economy.”
5️⃣ AI in National Security & Defense: A Smarter, Safer India 🛡️🚀
✅ AI in Cybersecurity — Advanced threat detection & prevention. ✅ AI-powered Surveillance & Defense Tech — Strengthening India’s armed forces. ✅ AI in Disaster Management — Early warning systems & crisis response automation.
“AI is the force multiplier for India’s defense and security strategy in the 21st century.”
🚀 The Road Ahead: Col Rathore’s Action Plan for AI-Driven Growth
🔹 AI Policy & Infrastructure Development — Strengthening India’s AI ecosystem. 🔹 Public-Private Partnerships for AI Innovation — Encouraging global collaborations. 🔹 AI Talent & Research Investments — Making India a global hub for AI development. 🔹 Ethical AI & Responsible Innovation — Ensuring AI benefits all sections of society.
“AI is India’s gateway to a smarter, more efficient, and innovative future. Let’s lead the way!” 🚀
🌍 India’s AI Future: Leading the Global Innovation Wave
✅ AI-powered industries, smart cities, and a digital economy. ✅ Next-gen job creation & future-ready workforce. ✅ Stronger governance, national security, and agriculture. ✅ A global AI leader driving innovation & inclusivity.
🔥 “AI is not just a tool — it’s the future. And India will lead it!” 🤖 Jai Hind! Jai Innovation! 🇮🇳🚀
4 notes
·
View notes
Text
The digital age has revolutionized how information is created, shared, and consumed, with crowdsourcing emerging as a powerful tool for problem-solving and knowledge dissemination. Crowdsourcing, which relies on collective intelligence and the active participation of individuals, has driven innovation in fields ranging from disaster response to product development. However, the rise of fake news—false or misleading information presented as fact—poses a significant threat to the integrity and reliability of crowdsourced data. The widespread dissemination of misinformation can erode trust, distort collective understanding, and undermine the very principles that make crowdsourcing effective.
One of the most profound effects of fake news on crowdsourced information is its ability to undermine trust and credibility.
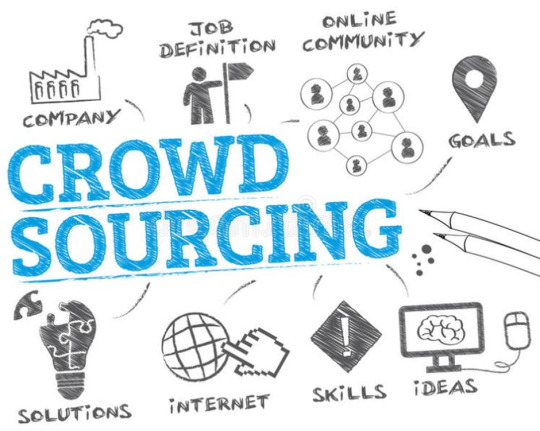
Crowdsourcing depends on participants’ willingness to contribute accurate data, ideas, or solutions. However, in an environment where fake news is pervasive, participants may grow skeptical about the validity of the information shared. This skepticism can deter people from engaging with crowdsourced platforms, fearing their contributions will be misused or overshadowed by false narratives. In cases where misinformation infiltrates these systems, the credibility of the entire project is jeopardized. For example, during crises like natural disasters or public health emergencies, crowdsourced data is often used to coordinate responses or allocate resources. If fake news contaminates this data, it can lead to harmful delays or misdirected efforts, putting lives at risk.
The rapid and viral nature of fake news further exacerbates its impact on crowdsourcing. Open-access platforms, where contributions are often unverified, can unintentionally amplify misinformation. When users unknowingly or carelessly share inaccurate information, it can quickly become entrenched in the collective dataset. Algorithms and social media dynamics exacerbate this problem, as sensational or emotionally charged content tends to spread faster than accurate, measured information. A common example is crowdsourced reviews on platforms like Amazon or Yelp, where fake reviews can manipulate consumer perceptions, distort market competition, and mislead potential buyers. Similarly, in knowledge repositories like Wikipedia, misinformation introduced into articles can spread globally, perpetuating inaccuracies until detected and corrected.
Beyond misinforming the public, fake news can also deepen divisions and foster polarization. Crowdsourced platforms are designed to pool diverse perspectives and foster collaboration, but when misinformation infiltrates these spaces, it can create echo chambers where users reinforce biased narratives. This polarization undermines the collective wisdom that crowdsourcing aims to harness, as dialogue becomes fragmented and contentious rather than constructive. In politically or socially sensitive contexts, misinformation campaigns can turn collaborative platforms into battlegrounds, derailing efforts to solve pressing issues and driving participants further apart.

Despite these challenges, there are strategies to mitigate the impact of fake news on crowdsourced information. One essential approach is implementing robust verification mechanisms. Crowdsourced platforms can employ AI tools to detect and flag suspicious contributions or identify patterns indicative of misinformation. For instance, Wikipedia’s community-driven editorial model effectively maintains accuracy by engaging volunteers to verify edits and ensure that citations are reliable. These mechanisms not only enhance the quality of data but also rebuild trust in the system.
Educating contributors about media literacy is another critical safeguard. By equipping participants with the skills to evaluate sources critically and verify information before sharing, platforms can significantly reduce the likelihood of misinformation infiltrating their datasets. This education must go hand-in-hand with transparency. Platforms should clearly outline their processes for moderating content and correcting errors, as well as visibly acknowledge and address inaccuracies when they occur. Transparency fosters accountability and reassures users that the platform is committed to accuracy and reliability.
Community involvement is another powerful tool in maintaining the integrity of crowdsourced information. Trusted contributors or subject-matter experts can play an active role in moderating and validating user-generated content. Platforms like Reddit demonstrate the effectiveness of community-driven moderation in maintaining the quality and authenticity of discussions. Similarly, collaboration with independent fact-checking organizations can bolster the credibility of crowdsourced platforms. Fact-checkers provide third-party validation for contentious claims, ensuring that misinformation is identified and corrected swiftly.
Technology also offers solutions to the challenges posed by fake news. Advanced machine learning algorithms can analyze content for indicators of misinformation, such as a lack of credible sources or emotionally manipulative language. These tools can flag questionable contributions in real-time, preventing their spread before they become entrenched in the dataset. Combining these technologies with human oversight ensures a balanced approach to maintaining accuracy.
In conclusion, the rise of fake news presents significant challenges to the reliability of crowdsourced information in the digital age. Misinformation can erode trust, amplify inaccuracies, and polarize participants, threatening the effectiveness of crowdsourcing initiatives. However, by adopting proactive measures such as verification mechanisms, media literacy education, transparency, and community engagement, the integrity of crowdsourced platforms can be preserved. As digital technologies continue to evolve, fostering a culture of critical thinking and accountability will be essential to maintaining the power of collective intelligence. By addressing the impact of fake news head-on, crowdsourced information can remain a valuable tool for innovation, collaboration, and progress in the digital era.
2 notes
·
View notes
Text
How To Reduce 5G Cybersecurity Risks Surface Vulnerabilities

5G Cybersecurity Risks
There are new 5G Cybersecurity Risks technology. Because each 5G device has the potential to be a gateway for unauthorized access if it is not adequately protected, the vast network of connected devices provides additional entry points for hackers and increases the attack surface of an enterprise. Network slicing, which divides a single physical 5G network into many virtual networks, is also a security risk since security lapses in one slice might result in breaches in other slices.
Employing safe 5G Cybersecurity Risks enabled devices with robust security features like multi-factor authentication, end-to-end encryption, frequent security audits, firewall protection, and biometric access restrictions may help organizations reduce these threats. Regular security audits may also assist in spotting any network vulnerabilities and taking proactive measures to fix them.
Lastly, it’s preferable to deal with reputable 5G service providers that put security first.
Take On New Cybersecurity Threats
Cybercriminals often aim their biggest intrusions at PCs. Learn the characteristics of trustworthy devices and improve your cybersecurity plan. In the current digital environment, there is reason for worry over the growing complexity and frequency of cyber attacks. Cybercriminals are seriously harming businesses’ reputations and finances by breaking into security systems using sophisticated tools and tactics. Being able to recognize and address these new issues is critical for both users and businesses.
Threats Driven by GenAI
Malicious actors find it simpler to produce material that resembles other individuals or entities more authentically with generative AI. Because of this, it may be used to trick individuals or groups into doing harmful things like handing over login information or even sending money.
Here are two instances of these attacks:
Sophisticated phishing: Emails and other communications may sound much more human since GenAI can combine a large quantity of data, which increases their credibility.
Deepfake: With the use of online speech samples, GenAI is able to produce audio and maybe even video files that are flawless replicas of the original speaker. These kinds of files have been used, among other things, to coerce people into doing harmful things like sending money to online fraudsters.
The mitigation approach should concentrate on making sure that sound cybersecurity practices, such as minimizing the attack surface, detection and response methods, and recovery, are in place, along with thorough staff training and continual education, even if both threats are meant to be challenging to discover. Individuals must be the last line of defense as they are the targeted targets.
Apart from these two, new hazards that GenAI models themselves encounter include prompt injection, manipulation of results, and model theft. Although certain hazards are worth a separate discussion, the general approach is very much the same as safeguarding any other important task. Utilizing Zero Trust principles, lowering the attack surface, protecting data, and upholding an incident recovery strategy have to be the major priorities.Image Credit To Dell
Ransomware as a Service (RaaS)
Ransomware as a Service (RaaS) lets attackers rent ransomware tools and equipment or pay someone to attack via its subscription-based architecture. This marks a departure from typical ransomware assaults. Because of this professional approach, fraudsters now have a reduced entrance barrier and can carry out complex assaults even with less technical expertise. There has been a notable rise in the number and effect of RaaS events in recent times, as shown by many high-profile occurrences.
Businesses are encouraged to strengthen their ransomware attack defenses in order to counter this threat:
Hardware-assisted security and Zero Trust concepts, such as network segmentation and identity management, may help to reduce the attack surface.
Update and patch systems and software on a regular basis.
Continue to follow a thorough incident recovery strategy.
Put in place strong data protection measures
IoT vulnerabilities
Insufficient security makes IoT devices susceptible to data breaches and illicit access. The potential of distributed denial-of-service (DDoS) attacks is increased by the large number of networked devices, and poorly managed device identification and authentication may also result in unauthorized control. Renowned cybersecurity researcher Theresa Payton has even conjured up scenarios in which hackers may use Internet of Things (IoT) devices to target smart buildings, perhaps “creating hazmat scenarios, locking people in buildings and holding people for ransom.”
Frequent software upgrades are lacking in many IoT devices, which exposes them. Furthermore, the deployment of more comprehensive security measures may be hindered by their low computational capacity.
Several defensive measures, such assuring safe setup and frequent updates and implementing IoT-specific security protocols, may be put into place to mitigate these problems. These protocols include enforcing secure boot to guarantee that devices only run trusted software, utilizing network segmentation to separate IoT devices from other areas of the network, implementing end-to-end encryption to protect data transmission, and using device authentication to confirm the identity of connected devices.
Furthermore, Zero Trust principles are essential for Internet of Things devices since they will continuously authenticate each user and device, lowering the possibility of security breaches and unwanted access.
Overarching Techniques for Fighting Cybersecurity Risks
Regardless of the threat type, businesses may strengthen their security posture by taking proactive measures, even while there are unique tactics designed to counter certain threats.
Since they provide people the skills and information they need to tackle cybersecurity risks, training and education are essential. Frequent cybersecurity awareness training sessions are crucial for fostering these abilities. Different delivery modalities, such as interactive simulations, online courses, and workshops, each have their own advantages. It’s critical to maintain training sessions interesting and current while also customizing the material to fit the various positions within the company to guarantee its efficacy.
Read more on govindhtech.com
#Reduce5G#CybersecurityRisks#5Gservice#ZeroTrust#generativeAI#cybersecurity#strongdata#onlinecourses#SurfaceVulnerabilities#GenAImodels#databreaches#OverarchingTechniques#technology#CybersecurityThreats#technews#news#govindhtech
2 notes
·
View notes
Text

The best 7 Genre to Start Writing in for 2024-2025
Here are descriptions of the seven genres you listed, tailored to trends and themes expected to resonate in 2024-2025:
1. Sci-Fi/Fantasy:
Sci-fi and fantasy are perfect for writers who love to imagine worlds beyond our current reality. For 2024-2025, speculative fiction is leaning toward themes like climate change, AI evolution, and dystopian futures. Fantasy continues to thrive with intricate world-building, magic systems, and epic quests, often reflecting real-world issues like diversity, politics, and power dynamics. Readers are drawn to the escapism but appreciate deeper themes that challenge societal norms.
2. Horror:
Horror writing is shifting toward psychological terror and societal fears. In 2024-2025, expect readers to be intrigued by stories that explore isolation, fear of the unknown, or threats lurking in the everyday. Modern horror also embraces supernatural elements or body horror while touching on social issues, making it a genre where scares are as much about the mind as about the monster. Tapping into cultural anxieties will resonate with audiences looking for both thrills and introspection.
3. Thriller/Crime Drama:
Fast-paced, tension-filled narratives are always in demand, and the coming years are no exception. From political conspiracies to personal revenge, thrillers and crime dramas appeal to readers who crave suspense. True crime influences and morally gray characters are trending, with more focus on flawed detectives or anti-heroes navigating a corrupt system. In 2024-2025, complex plot twists, unreliable narrators, and crimes rooted in current social issues will be key drivers of interest.
4. Romantic Dramas/Comedies:
Romance remains one of the most popular genres, and recent trends have focused on inclusivity and realism in love stories. Romantic dramas explore deep emotional journeys and relationships affected by external pressures. Comedies, on the other hand, balance romance with humor, often using quirky characters or unconventional pairings. For 2024-2025, readers are looking for stories with diverse characters, fresh dynamics, and themes like healing, second chances, and the challenges of modern dating.
5. Socially Relevant Dramas:
As people become more socially conscious, dramas centered on relevant topics are gaining traction. These stories delve into issues like inequality, immigration, climate change, mental health, and identity. The focus is on character-driven narratives that reflect real-world struggles, offering thoughtful commentary and emotional depth. For writers in 2024-2025, this genre allows you to engage with pressing issues while creating compelling, human stories that inspire empathy and action.
6. Murder Mystery:
The classic whodunit remains a staple in literature, but modern takes often blend genres or focus on psychological depth. In 2024-2025, murder mysteries are expected to become more complex, with layers of character backstories, secrets, and unreliable narrators. Readers love immersive puzzles, red herrings, and shocking twists, especially when set in unique or atmospheric locations. True crime elements and contemporary settings also breathe fresh life into the traditional format.
7. Docuseries/Non-Fiction:
Non-fiction writing has gained new momentum, especially in formats like docuseries-style storytelling. From personal memoirs to investigative journalism, the genre appeals to readers interested in true stories about real people or events. In 2024-2025, themes such as environmental crises, tech innovations, social justice, and cultural phenomena are likely to dominate. Writers can dive deep into research or share personal narratives, with the goal of educating, inspiring, or challenging the status quo.
Each of these genres offers vast opportunities for creativity, and by focusing on current trends, you’ll be able to connect with readers in fresh, meaningful ways.
Source -
2 notes
·
View notes
Text
High-Risk Payment Processing Techniques: Best Practices
Article by Jonathan Bomser | CEO | Accept-Credit-Cards-Now.com

In the ever-evolving realm of e-commerce, payment processing takes center stage, enabling businesses to smoothly accept credit card payments and ensure seamless customer transactions. However, for industries deemed high-risk, such as credit repair and CBD sales, navigating the payment processing landscape presents distinct challenges. In this article, we dive into the intricacies of high-risk payment processing methods and present best practices to guarantee secure and efficient transactions. Whether you're a newcomer to high-risk payment processing or looking to refine your current strategies, these insights will steer you toward favorable outcomes.
DOWNLOAD THE HIGH-RISK PAYMENT PROCESSING INFOGRAPHIC HERE
Understanding High-Risk Payment Processing Effective navigation of the high-risk payment processing sphere necessitates a clear comprehension of high-risk industries. Sectors like credit repair and CBD sales often fall into this category due to intricate regulations and an elevated risk of chargebacks. Consequently, high-risk merchants require specialized payment processing solutions tailored to mitigate associated risks.
The Importance of Merchant Accounts Merchant accounts form the backbone of efficient payment processing. These accounts, specifically designed for high-risk businesses, facilitate the secure transfer of funds from customers' credit cards to the merchant's bank account. Establishing a high-risk merchant account ensures seamless payment processing, enabling businesses to broaden their customer base and enhance revenue streams.
Exploring High-Risk Payment Gateways High-risk payment gateways serve as virtual checkpoints between customers and merchants. These gateways safeguard sensitive financial information by encrypting data during transactions. When selecting a high-risk payment gateway, emphasize security features and compatibility with your business model to guarantee safe and smooth payment processing.
Tailored Solutions for Credit Repair Businesses Credit repair merchants face unique challenges due to the industry's regulatory landscape. Obtaining a credit repair merchant account equipped with specialized payment processing solutions can aid in navigating these complexities. Implementing robust Know Your Customer (KYC) and Anti-Money Laundering (AML) procedures ensures compliance and fosters customer trust.
CBD Sales and Payment Processing CBD merchants operate in a market brimming with potential but also shrouded in uncertainty. Shifting regulations demand a flexible approach to CBD payment processing. Collaboration with experienced payment processors well-versed in the intricacies of CBD sales and the utilization of age verification systems can streamline transactions and bolster customer confidence.
Mitigating Chargeback Risks Chargebacks pose a significant threat to high-risk merchants, frequently arising from disputes, fraud, or unsatisfactory service. Proactively address this issue by providing exceptional customer support, transparent refund policies, and clear product descriptions. Consistent communication can forestall chargebacks and maintain a healthy merchant-consumer relationship.
youtube
Future-Proofing High-Risk Payment Processing Advancing technology necessitates the evolution of high-risk payment processing techniques to stay ahead of potential threats. Embrace emerging solutions like AI-driven fraud detection and biometric authentication to enhance security and streamline payment processing. Staying informed and adapting to industry trends ensures the future-proofing of payment processing strategies for high-risk merchants.
High-risk payment processing amalgamates industry knowledge, tailored solutions, and cutting-edge security measures. Whether operating in credit repair or CBD sales, a comprehensive understanding of high-risk payment processing intricacies is imperative. Leveraging specialized merchant accounts, payment gateways, and proactive chargeback prevention methods enables high-risk merchants to confidently accept credit card payments and cultivate long-term customer relationships. In an ever-evolving landscape, embracing innovative payment processing solutions guarantees a secure and prosperous future for high-risk businesses.
#high risk merchant account#high risk payment gateway#high risk payment processing#merchant processing#payment processing#credit card payment#credit card processing#accept credit cards#Youtube
17 notes
·
View notes